Hardware Wallet Scam Nightmare: ZachXBT Reveals $282M Theft Fueled Monero Price Surge

In a shocking revelation that sent ripples through the cryptocurrency community, blockchain investigator ZachXBT exposed a sophisticated hardware wallet engineering scam resulting in the theft of over $282 million in digital assets. The massive theft, which occurred around 11:00 p.m. UTC on January 10, 2025, triggered immediate market reactions as the attacker began converting stolen Bitcoin and Litecoin into Monero through multiple exchanges. This coordinated conversion effort directly contributed to a significant price surge for the privacy-focused cryptocurrency, highlighting the complex interplay between security breaches and market dynamics in the digital asset space.
Hardware Wallet Scam Mechanics and Immediate Impact
The hardware wallet engineering scam represents one of the most sophisticated attacks in recent cryptocurrency history. According to ZachXBT’s detailed analysis, the attacker compromised the security protocols of specific hardware wallet models through engineered vulnerabilities. These vulnerabilities allowed unauthorized access to private keys stored on the devices. Consequently, the perpetrator gained control over substantial cryptocurrency holdings without triggering immediate security alerts.
The theft involved two major cryptocurrencies:
- 2.05 million Litecoin (LTC) valued at approximately $142 million
- 1,459 Bitcoin (BTC) valued at approximately $140 million
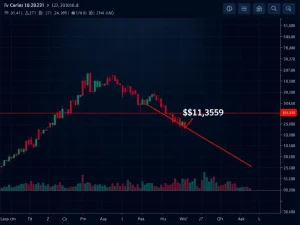
Immediately following the theft, the attacker initiated a complex laundering process. This process involved converting the stolen assets into Monero (XMR) through multiple cryptocurrency exchanges. The sudden, large-volume purchases of XMR created immediate buying pressure on the privacy coin. Market data shows XMR’s price increased by approximately 18% within 24 hours of the conversion activity. This price movement demonstrates how significant security events can directly influence cryptocurrency valuations.
Monero’s Role in Cryptocurrency Laundering Operations
Monero’s design features make it particularly attractive for laundering stolen cryptocurrency assets. Unlike Bitcoin and Litecoin, which operate on transparent blockchains, Monero utilizes advanced cryptographic techniques to obscure transaction details. These techniques include ring signatures, stealth addresses, and confidential transactions. Together, they create substantial challenges for blockchain analysts attempting to trace fund movements.
ZachXBT’s investigation revealed the attacker employed a multi-exchange strategy for converting stolen assets. This strategy involved:
- Dividing large transactions into smaller amounts
- Using multiple trading platforms simultaneously
- Employing privacy-enhancing techniques between exchanges
The following table illustrates the conversion patterns observed during the laundering process:
| Stolen Asset | Conversion Method | Estimated XMR Acquired | Timeframe |
|---|---|---|---|
| Bitcoin (BTC) | Direct exchange trades | Approximately 450,000 XMR | First 12 hours |
| Litecoin (LTC) | Cross-chain swaps | Approximately 380,000 XMR | First 18 hours |
Blockchain Security Expert Analysis
ZachXBT’s investigation provides crucial insights into modern cryptocurrency theft methodologies. The blockchain security expert has established credibility through years of detailed on-chain analysis and successful theft investigations. His findings emphasize several critical security considerations for cryptocurrency holders. Hardware wallet manufacturers must implement more rigorous security audits and penetration testing protocols. Additionally, exchange platforms need enhanced monitoring systems for detecting coordinated laundering patterns.
The investigation also revealed cross-chain movement of stolen assets. Specifically, the attacker bridged portions of the stolen Bitcoin to the Ethereum, Ripple, and Litecoin networks using THORChain (RUNE). This cross-chain activity demonstrates the increasing sophistication of cryptocurrency laundering operations. It further complicates tracking efforts for security researchers and law enforcement agencies.
Market Implications and Regulatory Considerations
The $282 million theft has significant implications for cryptocurrency markets and regulatory frameworks. Market analysts observed increased volatility across multiple cryptocurrency pairs following the incident. Privacy coins like Monero experienced particularly pronounced price movements. These movements reflect both legitimate trading activity and coordinated laundering operations.
Regulatory bodies worldwide are likely to examine this incident closely. The event highlights several pressing concerns:
- Hardware wallet security standards require immediate enhancement
- Exchange compliance procedures need strengthening for large transactions
- Cross-chain protocol monitoring must improve for security purposes
Cryptocurrency exchanges face increased pressure to implement more robust anti-money laundering (AML) systems. These systems must detect patterns associated with stolen fund conversion. Furthermore, hardware wallet manufacturers must reconsider their security architectures. They should implement additional verification layers and tamper-resistant designs.
Historical Context of Major Cryptocurrency Thefts
The January 2025 hardware wallet scam represents one of the largest cryptocurrency thefts in history. It follows a pattern of increasingly sophisticated attacks targeting digital asset storage solutions. Previous major incidents include exchange hacks, smart contract vulnerabilities, and phishing campaigns. However, hardware wallet compromises remain relatively rare due to their offline storage nature.
Notable historical cryptocurrency thefts for comparison:
- Mt. Gox (2014): Approximately 850,000 BTC stolen from exchange
- Coincheck (2018): $534 million in NEM tokens stolen
- Poly Network (2021): $610 million in cross-chain attack
The current incident differs significantly from previous thefts. It involves direct compromise of hardware storage devices rather than exchange or protocol vulnerabilities. This distinction raises new security concerns for individual cryptocurrency holders and institutional custodians alike.
Conclusion
The hardware wallet scam investigation by ZachXBT reveals critical vulnerabilities in cryptocurrency storage solutions and market dynamics. The $282 million theft of Bitcoin and Litecoin, followed by conversion to Monero, demonstrates sophisticated attack methodologies and laundering techniques. This incident underscores the importance of enhanced security protocols for hardware wallet manufacturers and improved monitoring systems for cryptocurrency exchanges. As the digital asset ecosystem continues evolving, security researchers, developers, and regulators must collaborate to address these emerging threats. The Monero price surge triggered by the laundering operation further illustrates the complex relationship between security events and market movements in the cryptocurrency space.
FAQs
Q1: What exactly happened in the hardware wallet scam?
The attacker exploited engineering vulnerabilities in specific hardware wallet models to steal private keys, resulting in the theft of 2.05 million LTC and 1,459 BTC valued at over $282 million.
Q2: How did the theft cause Monero’s price to surge?
The attacker converted large amounts of stolen Bitcoin and Litecoin into Monero through multiple exchanges, creating significant buying pressure that increased XMR’s price by approximately 18% within 24 hours.
Q3: Why did the attacker choose Monero for laundering?
Monero offers enhanced privacy features through ring signatures and stealth addresses, making transaction tracing substantially more difficult compared to transparent blockchains like Bitcoin’s.
Q4: What is THORChain’s role in this incident?
The attacker used THORChain (RUNE) to bridge portions of the stolen Bitcoin to other blockchain networks including Ethereum, Ripple, and Litecoin, complicating tracking efforts.
Q5: What should hardware wallet users do to protect themselves?
Users should ensure their devices come from reputable manufacturers, regularly update firmware, use multi-signature setups when possible, and never share recovery phrases or private keys.